Add AKS clusters
Prerequisites
Before adding your AKS cluster to Portworx Backup:
Your cluster must be running Stork 2.10 or higher. To install Stork on your Kubernetes cluster, copy and paste the command displayed below the Kubernetes Service radio group.
curl -fsL -o stork-spec.yaml "https://install.portworx.com/pxbackup?comp=stork&storkNonPx=true" kubectl apply -f stork-spec.yamlEnsure that you have a storage account in Azure.
Add Azure cloud account in Portworx Backup and then add Azure backup location.
Add Azure Cloud Account
To add an Azure cloud account in Portworx Backup we need these parameters:
Cloud account name: a cloud account name of your preference
Storage account name: check Azure portal
Storage account key: run the below command
az storage account list |grep <storage_account_name> az storage account keys list --resource-group <resource_group_name> --account-name <storage_account_name>Output:
az storage account keys list --resource-group "resource_group_name"--account-name "storage_account_name" [ { "creationTime": null, "keyName": "key1", "permissions": "FULL", "value": "azure-storage-account-key1" }, { "creationTime": null, "keyName": "key2", "permissions": "FULL", "value":"azure-storage-account-key2" } ]NOTE: You can pick any one of the key values as the storage account key from this output. Alternatively, you can also get the account key details from the Azure cloud portal.Subscription ID: run the below command
az account subscription listClient ID, Client Secret, and Tenant ID: to fetch these three values, you need to create a custom role, fetch AKS infrastructure resource group name and then create a service principal.
a. To create a custom role for Portworx Backup, copy the below content to a json file and save it to any of your root directory. Specify a name for custom role and enter subscription ID.
'{ "Name": "<custom_role_name>", "Description": "", "AssignableScopes": [ "/subscriptions/<subscription_ID>" ], "Permissions": [ { "Actions": [ "Microsoft.Compute/snapshots/read", "Microsoft.Compute/snapshots/write", "Microsoft.Compute/snapshots/delete", "Microsoft.Compute/snapshots/beginGetAccess/action", "Microsoft.Compute/snapshots/endGetAccess/action", "Microsoft.Compute/diskAccesses/read", "Microsoft.Compute/diskAccesses/write", "Microsoft.Compute/diskAccesses/delete", "Microsoft.Compute/diskAccesses/privateEndpointConnectionsApproval/action", "Microsoft.Compute/locations/diskOperations/read", "Microsoft.Compute/disks/write", "Microsoft.Compute/disks/read", "Microsoft.Compute/disks/delete", "Microsoft.Compute/disks/beginGetAccess/action", "Microsoft.Compute/disks/endGetAccess/action", "Microsoft.Compute/restorePointCollections/restorePoints/diskRestorePoints/read", "Microsoft.Compute/restorePointCollections/restorePoints/diskRestorePoints/beginGetAccess/action", "Microsoft.Compute/restorePointCollections/restorePoints/diskRestorePoints/endGetAccess/action", "Microsoft.StoragePool/locations/diskPoolZones/read", "Microsoft.StoragePool/diskPools/read", "Microsoft.StoragePool/diskPools/write", "Microsoft.StoragePool/diskPools/delete", "Microsoft.StoragePool/diskPools/start/action", "Microsoft.StoragePool/diskPools/deallocate/action", "Microsoft.StoragePool/diskPools/upgrade/action", "Microsoft.StoragePool/diskPools/iscsiTargets/read", "Microsoft.StoragePool/diskPools/iscsiTargets/write", "Microsoft.StoragePool/diskPools/iscsiTargets/delete", "Microsoft.Compute/diskAccesses/privateEndpointConnectionProxies/read", "Microsoft.Compute/diskAccesses/privateEndpointConnectionProxies/write", "Microsoft.Compute/diskAccesses/privateEndpointConnectionProxies/delete", "Microsoft.Compute/diskAccesses/privateEndpointConnectionProxies/validate/action", "Microsoft.Compute/diskAccesses/privateEndpointConnections/delete", "Microsoft.Compute/diskAccesses/privateEndpointConnections/read", "Microsoft.Compute/diskAccesses/privateEndpointConnections/write", "Microsoft.Compute/virtualMachineScaleSets/reimageAll/action", "Microsoft.Compute/virtualMachineScaleSets/virtualMachines/reimageAll/action", "Microsoft.Compute/virtualMachines/capture/action", "Microsoft.Compute/virtualMachines/convertToManagedDisks/action", "Microsoft.Compute/virtualMachines/reimage/action", "Microsoft.Storage/storageAccounts/updateInternalProperties/action", "Microsoft.Storage/storageAccounts/hnsonmigration/action", "Microsoft.Storage/storageAccounts/restoreBlobRanges/action", "Microsoft.Storage/storageAccounts/PrivateEndpointConnectionsApproval/action", "Microsoft.Storage/storageAccounts/failover/action", "Microsoft.Storage/storageAccounts/listkeys/action", "Microsoft.Storage/storageAccounts/regeneratekey/action", "Microsoft.Storage/storageAccounts/rotateKey/action", "Microsoft.Storage/storageAccounts/revokeUserDelegationKeys/action", "Microsoft.Storage/storageAccounts/delete", "Microsoft.Storage/storageAccounts/read", "Microsoft.Storage/storageAccounts/listAccountSas/action", "Microsoft.Storage/storageAccounts/listServiceSas/action", "Microsoft.Storage/storageAccounts/write", "Microsoft.Storage/storageAccounts/accountMigrations/read", "Microsoft.Storage/storageAccounts/accountMigrations/write", "Microsoft.Storage/storageAccounts/inventoryPolicies/delete", "Microsoft.Storage/storageAccounts/inventoryPolicies/read", "Microsoft.Storage/storageAccounts/inventoryPolicies/write", "Microsoft.Storage/storageAccounts/restorePoints/delete", "Microsoft.Storage/storageAccounts/restorePoints/read", "Microsoft.Storage/storageAccounts/fileServices/shares/action", "Microsoft.Storage/storageAccounts/fileServices/read", "Microsoft.Storage/storageAccounts/fileServices/write", "Microsoft.Storage/storageAccounts/fileServices/shares/delete", "Microsoft.Storage/storageAccounts/fileServices/shares/read", "Microsoft.Storage/storageAccounts/fileServices/shares/lease/action", "Microsoft.Storage/storageAccounts/fileServices/shares/write", "Microsoft.Storage/storageAccounts/objectReplicationPolicies/delete", "Microsoft.Storage/storageAccounts/objectReplicationPolicies/read", "Microsoft.Storage/storageAccounts/objectReplicationPolicies/write", "Microsoft.Storage/storageAccounts/objectReplicationPolicies/restorePointMarkers/write", "Microsoft.Storage/storageAccounts/managementPolicies/delete", "Microsoft.Storage/storageAccounts/managementPolicies/read", "Microsoft.Storage/storageAccounts/managementPolicies/write" ], "NotActions": [], "DataActions": [], "NotDataActions": [] } ] }'b. Now create a role by invoking the json file:
az role definition create --role-definition px-backup-roles.jsonOutput:
{ "assignableScopes": [ "/subscriptions/<subscription-id>" ], "description": "", "id": "/subscriptions/<subscription-id>/providers/Microsoft.Authorization/roleDefinitions/<role_definition>", "name": "<role_definition>", "permissions": [ { "actions": [], "dataActions": [], "notActions": [], "notDataActions": [] } ], "roleName": "<custom_role_name>", "roleType": "CustomRole", "type": "Microsoft.Authorization/roleDefinitions" }c. Fetch AKS Infrastructure Resource Group name:
az aks show -n <aks_cluster_name> -g <resource_group_name> | jq -r '.nodeResourceGroup'd. Create a service principal for Portworx Backup custom role:
az ad sp create-for-rbac --role=<custom_role_name> --scopes="/subscriptions/<subscription_ID>/resourceGroups/<aks_infrastructure_resource_group_name>"Output:
{ "appId": "client_ID", "displayName": "px-backup-rbac", "password": "client_secret", "tenant": "tenant_ID" }App ID is the Client ID, password is the Client Secret and tenant is the Tenant ID values.
Alternatively you can use the below command to generate Tenant ID alone:az account tenant listSubscription ID can be obtained from the 4th row of this table.
You can now add an Azure cloud account in Portworx Backup with the inputs obtained from the above steps.
Add the cluster to Portworx Backup
From the home page, select Add Cluster:
In the Add Cluster page, under Select Kubernetes Platform, select Azure and then enter the cluster details:
- The name of the cluster.
- Retrieve the Kubeconfig from your cluster and paste it in the Kubeconfig text frame, or click Browse to upload it from a file.
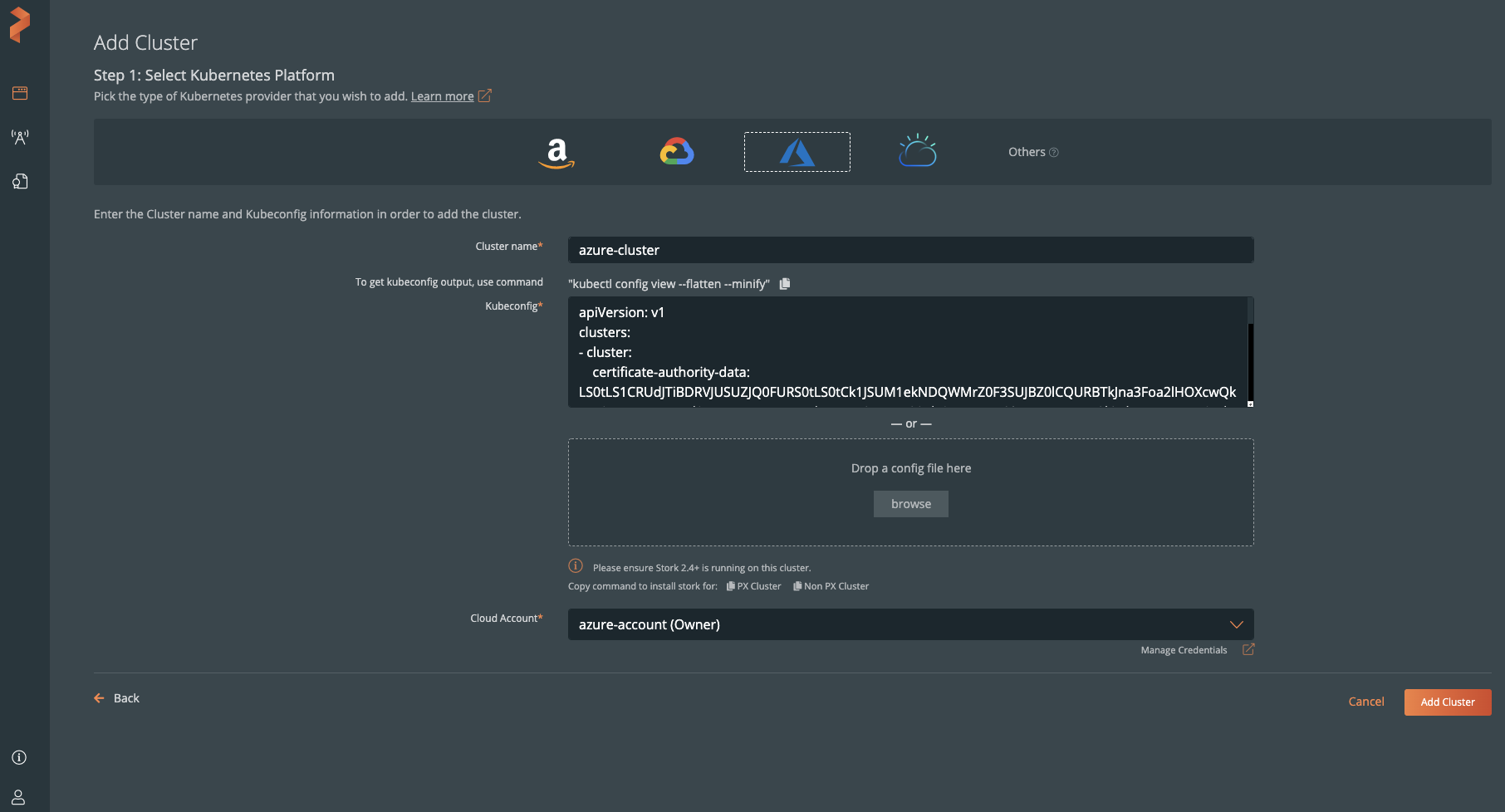
Choose the cloud account you added earlier.
Click Add Cluster.
